ACH Payments
Unlocking the Potential of ACH Payments and Transactions

The Impact of ACH Payments on Modern Finance
Why Use ACH?
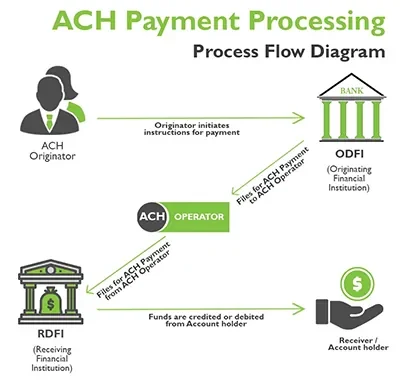
- Authorization: The process begins with authorization from the sender (originator) to initiate the ACH transaction.
- Initiation: The originator initiates the ACH transaction by providing payment instructions to their bank or a third-party service provider.
- Batch Processing: ACH transactions are typically processed in batches rather than individually.
- Transmission: The batch file is transmitted to the ACH operator, which is responsible for routing the transactions to the appropriate receiving banks.
- Routing and Settlement: The ACH operator routes each transaction to the recipient’s bank based on the bank’s routing number.
- Confirmation: Once the transaction is processed and settled, both the originator and the recipient receive confirmation of the transaction.
Throughout the process, ACH transactions are governed by rules and regulations set forth by organizations such as the National Automated Clearing House Association (NACHA), which oversees the ACH network in the United States. These rules ensure the security, efficiency, and reliability of ACH transactions, making them a trusted and widely used method of electronic payment.

Security and ACH
- Encryption: ACH transactions are encrypted using advanced encryption algorithms, which scramble data during transmission to prevent unauthorized access or interception. This ensures that sensitive information, such as bank account numbers and transaction details, remains secure while in transit.
- Authentication: ACH transactions require authentication to verify the identity of parties involved in the transaction. This may involve the use of secure access credentials, such as usernames, passwords, or cryptographic keys, to ensure that only authorized users can initiate or approve transactions.
- Authorization Controls: ACH transactions often require multiple levels of authorization to prevent unauthorized or fraudulent transactions. Businesses may implement authorization controls, such as approval workflows or dual authorization requirements, to ensure that transactions are valid and authorized by appropriate personnel.
- Fraud Detection and Monitoring: Financial institutions employ sophisticated fraud detection and monitoring systems to identify suspicious activity and potential instances of fraud within the ACH network. These systems analyze transaction patterns, monitor account activity in real time, and flag any anomalies or suspicious behavior for further investigation.
- Regulatory Compliance: The ACH network is subject to stringent regulatory requirements and industry standards designed to safeguard the security and integrity of electronic transactions. Regulatory bodies, such as the National Automated Clearing House Association (NACHA), establish rules and guidelines that financial institutions must adhere to, ensuring compliance with security best practices and data protection regulations.
- Risk Management: Financial institutions and payment processors implement robust risk management practices to mitigate the risk of fraud and financial losses associated with ACH transactions. This includes monitoring transaction activity, assessing risk profiles, and implementing controls to prevent unauthorized transactions or mitigate potential losses.
Overall, the ACH network employs a multi-layered approach to security, incorporating encryption, authentication, authorization controls, fraud detection, regulatory compliance, and risk management practices to protect against unauthorized access, fraud, and other security threats. These security measures help instill confidence in the ACH system and ensure the safe and secure processing of electronic payments.
Embracing the Power of ACH Payments with Instant Accept
In conclusion, embracing the power of ACH payments with Instant Accept presents a transformative opportunity for businesses and individuals alike. By leveraging the speed, security, and cost-effectiveness of ACH transactions, businesses can streamline their financial processes, reduce overheads, and improve cash flow management. With Instant Accept’s user-friendly platform, the integration of ACH payments becomes seamless, allowing businesses to focus on growth and innovation while providing customers with a convenient and reliable payment experience. As we move forward in the digital age, embracing ACH payments and Instant Accept is not just about keeping up—it’s about staying ahead and unlocking the full potential of modern financial technology.
Find Out if ACH Payments are Right for You.
Contact us to learn more about our ACH Payment options, click the button below to contact one of our sales representatives. They will be happy to help and answer any questions you may have.